Active Directory Integration
Synchronizing User Accounts with Active Directory
In addition to adding users manually (as described in chapter "User Management"), MailStore can synchronize its internal user database with the Active Directory of your company.
During synchronization, user information and email addresses are gathered from Active Directory and recorded in MailStore; no changes are made to Active Directory.
Accessing Active Directory Integration
Log on to MailStore Client as administrator. Click on Administrative Tools and then on Active Directory Integration.
Specifying Connection Settings
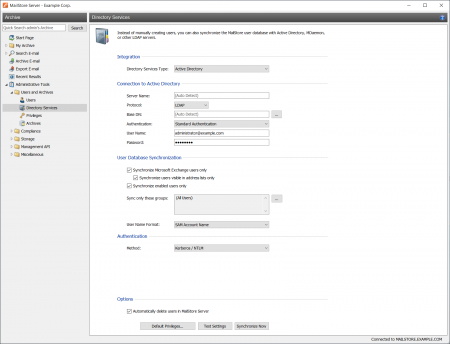
Before the synchronization can be started, MailStore requires information on how to connect to the Active Directory server. In most cases it should be sufficient to click on Auto-Detect All Settings. If successful, the following fields are filled out automatically.
Under Authentication, specify which user identification is to be used to access Active Directory.
Executing the Synchronization
Under User Database Synchronization, after the connection settings have been specified (as described above), the MailStore user list can be synchronized with the Active Directory user list.
The following options are available:
- Automatically create new users in MailStore
Clear this checkbox if, during Active Directory synchronization, no new users are to be created in MailStore. In this case, only the data of already existing MailStore users is updated.
- Synchronize Microsoft Exchange users only
Clear this checkbox only if all Active Directory users are to be created in MailStore as well.
- Synchronize only members of a group
Clear this Checkbox and enter a group name, if you want only members of that Active Directory group to be synchronized with you Mailstore Server.
To start, click on Synchronize Now.
Click on Simulate Only to see what would happen during actual synchronization. Background: Which Information is Copied?
If a user who does not yet exist in MailStore is located in Active Directory, the following steps are executed:
- A new MailStore user is created with the login name (SAM account name) of the Active Directory user.
- LDAP Authentication is configured for the new MailStore user. Additional information about this topic is available in section Login with Window Access Data.
- The MailStore user has the following privileges: Logging on to MailStore Server through MailStore Client, archiving new emails for his or her own user archive, browsing his or her archive and viewing the emails contained therein. The user does not have the privilege to delete emails from the archive.
The following steps are executed for all users (new and existing) during synchronization:
- The full name of the MailStore user is replaced with the full name of the Active Directory user.
- All email addresses assigned to the MailStore user are replaced with the email addresses entered in Active Directory:
If the user is a Microsoft Exchange user, this concerns all his or her SMTP addresses. If the user is not a Microsoft Exchange user, this concerns the address entered under Email Address.
Synchronizing Small Business Server Users Only
When using Microsoft's Small Business Server, Windows system users are added to MailStore's user management along with the settings that are automatically specified. In most cases, adding Windows system users to MailStore is undesirable.
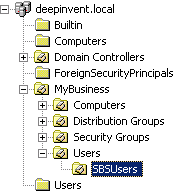
To limit the synchronization process to the users created with the Small Business Server Assistant, specify the organizational unit SBUsers as base DN:
Simply add the corresponding branches to the left of the automatically recognized base DN:
OU=SBSUsers,OU=Users,OU=MyBusiness,DC=deepinvent,DC=local
Automating the Synchronization with ADS_SYNC
To automate the synchronization, the command ads-sync can be used in MailStore's Management Shell. Information about how to use and automatically execute management shell commands is available in chapter The MailStore Management Shell.
ads-sync has the following parameters:
--server=<ldap-server> Indicates the LDAP-Server (Active Directory) to be contacted
--domain=<netbiosdomain> Indicates the NETBIOS domain name (prior to Windows 2000) --user=<username> Indicates the user to be used in the LDAP connection
--pass=<password> Indicates the password to be used in the LDAP connection
--allow-create Use the allow-create switch if new users are to be created in MailStore. If this switch is not set, only the information of already existing users will be updated.
Login with Windows Credentials
By default, each MailStore user has a password exclusively for MailStore which the administrator can specify during creation of a new user account. In MailStore Client's Administrative Tools, the respective user can later change his or her password.
Alternatively, if Active Directory is available, MailStore can be configured to allow users to log on to MailStore Server through MailStore Client using their Active Directory password.
Procedure for Users Created During Synchronization with Active Directory
If the MailStore users were created using Active Directory Synchronization, as described in the previous section, no further action is required. In this case, MailStore has already specified all necessary settings automatically. Procedure for Manually Created Users
If MailStore users who were created manually are to be able to log on using their Active Directory password, please proceed as follows:
- Configure the Active Directory Integration as described in chapter Synchronizing User Accounts with Active Directory.
- Verify that the names of the MailStore users match those of the corresponding Active Directory users.
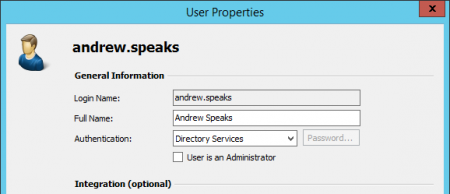
- In the User Properties window under Authentication, select LDAP (Active Directory).
Background: How MailStore Proceeds Internally when Using LDAP Authentication
The following section describes how MailStore proceeds during LDAP authentication. This description is addressed to users interested in technical details.
- The user logs on; access data is sent to MailStore Server.
- MailStore Server verifies that this is a user for whom LDAP-Authentication is configured.
- MailStore establishes a secure LDAP connection to the Active Directory Server configured in Active Directory Integration. MailStore uses a user name consisting of the Domain (NetBIOS), also specified under Active Directory Integration, and the MailStore user name (DOMAIN\user).
- If the connection can be opened, MailStore Server searches for the user name (sAMAccountName) under Base DN which is configured in Active Directory Integration. If the name is found, MailStore Server regards the access data as being correct.
- If the LDAP authentication was successful, the user is logged on to MailStore Server as usual.
MailStore Client Single Sign-On
For using the single sign-on functionality in Active Directory environments, MailStore Server provides an ADM template.
The MailStore Client ADM Template (administrative template) makes it possible to configure the MailStore Client login using the group policy editor. The ADM template is located in the Support subfolder of the MailStore Server program folder
Using a group policy, the ADM template can be distributed among all Windows clients in your Active Directory network who are to use the single sign-on functionality.
The Group Policy Management Console
The distribution of group policies among online clients is a basic function offered by every Active Directory-based network. Setup of a group policy for single sign-on is described based on the Group Polity Management Console (GPMC). Starting with Windows Server 2007, the management console is an optional component of the server installation; the installation routine for Windows 2003 can be downloaded under http://www.mailstore.com/?gpmc.
Installing the ADM Template in Active Directory
- Open the group policy management console.
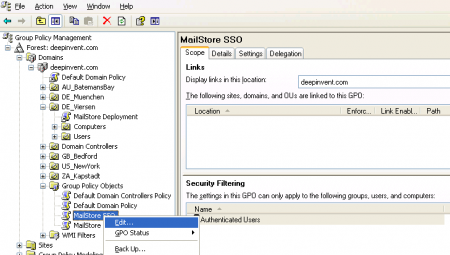
- Right-click on the administrative folder Group Policy Objects, select New and create a new group policy object called MailStore SSO.
- Highlight the new object and click on Edit.
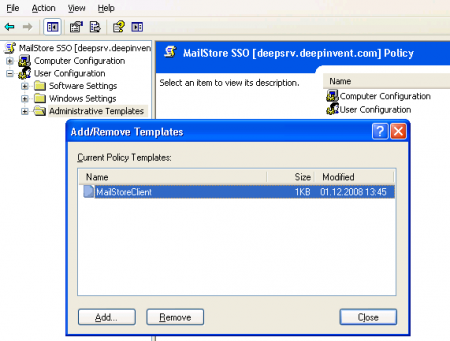
- Expand User Configuration and highlight Administrative Templates. Click on Add/Remove Templates.
- Click on Add and select the administrative template MailStoreClient.adm. It can be found in the Support subfolder of the MailStore Server program folder. Remove all policy templates that may still be listed and close the window.
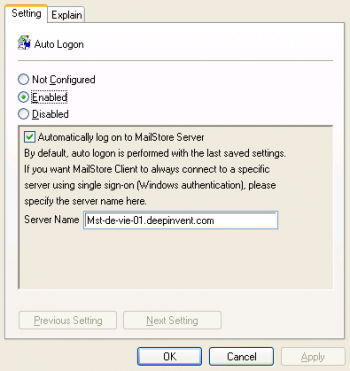
- Expand Administrative Templates, click on MailStore Client and edit the entry Auto Logon.
- Enable the setting, check the option to Automatically log on to MailStore Server and in the field Server Name, enter the DNS name of the MailStore Server computer
Please note: If single sign-on does not work with these settings, please enter the IP address of MailStore Server instead of the name.
- Click on OK and close the group policy editor. The group policy is now configured and can be linked to the corresponding user objects. This is done using organizational units (OU).
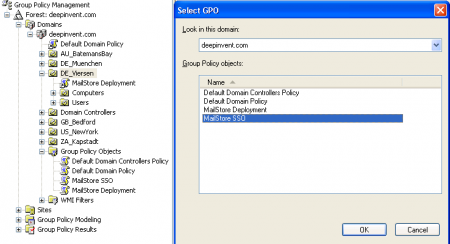
- Highlight and then right-click on the organizational unit which contains the desired user objects (DE_Viersen in the example above) and select the option Link an Existing GPO. In the dialog window Select GPO, highlight the MailStore SSO policy and confirm by clicking OK.
- The group policy does now exist and will become active the next time users log on to the Windows clients.