Difference between revisions of "Multi-factor Authentication"
| [unchecked revision] | [checked revision] |
Ltalaschus (talk | contribs) (Created page with "To increase security during the login process, multi-factor authentication (MFA) can be activated for users with ''MailStore-integrated'' authentication. MailStore supports ''...") |
Ltalaschus (talk | contribs) |
||
| (6 intermediate revisions by 2 users not shown) | |||
| Line 1: | Line 1: | ||
| − | To increase security during the login process, multi-factor authentication (MFA) can be activated for users | + | To increase security during the login process, multi-factor authentication (MFA) can be activated for MailStore users. MailStore supports ''Time-based One-time Password (TOTP)'' according to ''RFC 6238''.<br/><br/> |
| − | To do this, users need a TOTP- | + | To do this, users need a TOTP-capable device, e.g. a smartphone with an installed authenticator app.<br/><br/> |
| + | MailStore does not request the second factor, when the user is authenticated by Windows Authentication (Single Sign-On) or OpenID Connect (Microsoft 365, ADFS, Google Workspace).<br/><br/> | ||
| + | When MFA is enabled, users who authenticate against a directory service cannot utilize non-MFA-capable clients such as Scheduled Tasks, IMAP clients, or the Management API. This restriction is in place for security reasons. Due to MailStore’s internal management of app passwords (which are necessary for non-MFA-capable clients), a user could still log in to MailStore even if they are blocked in the directory service. | ||
<p class=msnote>'''Important notice:''' In order for valid one-time passwords (TOTP) to be generated, the system times of the MailStore Server and the end devices must be synchronized.</p> | <p class=msnote>'''Important notice:''' In order for valid one-time passwords (TOTP) to be generated, the system times of the MailStore Server and the end devices must be synchronized.</p> | ||
| Line 6: | Line 8: | ||
== Configuration == | == Configuration == | ||
| − | Administrators are able to configure multi-factor authentication | + | Administrators are able to configure multi-factor authentication within [[Users,_Folders_and_Settings|user management]]. |
Log in as a MailStore administrator via MailStore Client. Click ''Administrative Tools'' > ''Users and Archives'' and then click ''Users''. | Log in as a MailStore administrator via MailStore Client. Click ''Administrative Tools'' > ''Users and Archives'' and then click ''Users''. | ||
| Line 13: | Line 15: | ||
* Open the properties of the user you want to enable MFA for. | * Open the properties of the user you want to enable MFA for. | ||
| − | * | + | * Check the option ''Multi-factor Authentication'' in the ''General Information'' section. |
* Confirm with ''OK''. | * Confirm with ''OK''. | ||
| − | * The next time the user [[Multi- | + | * The next time the user [[Multi-factor_Authentication#Login|logs in]] with an MFA-capable client (MailStore Client, MailStore Outlook Add-In, Web Access), the user will be prompted to scan a QR code with a TOTP-capable authenticator app (e.g. Google Authenticator), then enter an MFA code to complete the MFA configuration. |
[[File:umgm_users_02_mfa.png|center|400px]] | [[File:umgm_users_02_mfa.png|center|400px]] | ||
| Line 22: | Line 24: | ||
* Open the properties of the user you want to disable MFA for. | * Open the properties of the user you want to disable MFA for. | ||
| − | * | + | * Uncheck the option ''Multi-factor Authentication'' in the ''General Information'' section. |
* Confirm with ''OK''. | * Confirm with ''OK''. | ||
* App passwords that may have been created remain in place and remain valid. | * App passwords that may have been created remain in place and remain valid. | ||
| Line 31: | Line 33: | ||
If a user lost the device on which MFA was set up, wants to set up MFA on a different device, or needs to set up MFA again for some other reason, you can reinitialize MFA. This generates a new secret from which the one-time passwords are derived.<br/> | If a user lost the device on which MFA was set up, wants to set up MFA on a different device, or needs to set up MFA again for some other reason, you can reinitialize MFA. This generates a new secret from which the one-time passwords are derived.<br/> | ||
| − | The next time the user [[Multi- | + | The next time the user [[Multi-factor_Authentication#Login|logs in]], they will be prompted again to complete the MFA configuration. |
<br/> | <br/> | ||
If the user has not yet completed the MFA configuration with their device, this function is not available. | If the user has not yet completed the MFA configuration with their device, this function is not available. | ||
| Line 44: | Line 46: | ||
=== Delete App passwords === | === Delete App passwords === | ||
| − | If a user has created app passwords to continue using ''non- | + | If a user has created app passwords to continue using ''non MFA-capable clients'' (Scheduled Tasks, IMAP, Management API), you can delete them here. |
<br/> | <br/> | ||
If the user has not created any app passwords, this feature is not available. | If the user has not created any app passwords, this feature is not available. | ||
| Line 57: | Line 59: | ||
== Login == | == Login == | ||
| − | If multi-factor authentication has been activated for a user, the next time the user logs in with an MFA- | + | If multi-factor authentication has been activated for a user, the next time the user logs in with an MFA-capable client (MailStore Client, MailStore Outlook Add-In, Web Access), the user will be prompted to scan a QR code with a TOTP-capable authenticator app (e.g. Google Authenticator). This stores the previously generated secret into the app, and the app is able to generate valid one-time passwords.<br/> |
The secret is displayed below the QR code and can be copied to the clipboard with a double-click to be stored in a password manager. | The secret is displayed below the QR code and can be copied to the clipboard with a double-click to be stored in a password manager. | ||
| Line 74: | Line 76: | ||
MailStore Client, Outlook Add-In and Web Access each save their own token.<br/><br/> | MailStore Client, Outlook Add-In and Web Access each save their own token.<br/><br/> | ||
The token for MailStore Client and the Outlook Add-In is stored in the Windows credential manager. It does not move with roaming profiles.<br/><br/> | The token for MailStore Client and the Outlook Add-In is stored in the Windows credential manager. It does not move with roaming profiles.<br/><br/> | ||
| − | The token for | + | The token for Web Access is stored in the browser's ''Local Storage''. When Web Access is accessed in the browser's ''Incognito mode'', the token is not persisted in between browser sessions. |
== Management of app passwords == | == Management of app passwords == | ||
| − | Once multi-factor authentication has been enabled for a user, the normal password can no longer be used to log in with ''non- | + | Once multi-factor authentication has been enabled for a user, the normal password can no longer be used to log in with ''non MFA-capable clients''.<br/><br/> |
| − | ''Non- | + | ''Non MFA-capable clients'' include:<br/> |
* ''[[Email_Archiving_with_MailStore_Basics#Automating_Execution_of_E-mail_Client_or_E-mail_Files_Archiving_Profiles|Scheduled Tasks]]'', that use the MailStore Client in command line mode | * ''[[Email_Archiving_with_MailStore_Basics#Automating_Execution_of_E-mail_Client_or_E-mail_Files_Archiving_Profiles|Scheduled Tasks]]'', that use the MailStore Client in command line mode | ||
* [[Accessing_the_Archive_via_Integrated_IMAP_Server|IMAP clients]] | * [[Accessing_the_Archive_via_Integrated_IMAP_Server|IMAP clients]] | ||
| Line 87: | Line 89: | ||
App passwords can only be managed via MailStore Client by users with ''MailStore-integrated'' authentication. In addition, the ''Change Password'' right is required.<br/> | App passwords can only be managed via MailStore Client by users with ''MailStore-integrated'' authentication. In addition, the ''Change Password'' right is required.<br/> | ||
| − | App passwords work even with MFA disabled. | + | App passwords work even with MFA disabled.<br/> |
| + | App passwords can never be used to login with MFA-capable clients. | ||
| − | * Log on to [[ | + | * Log on to [[Accessing_the_Archive_with_the_MailStore_Client_software|MailStore Client]]. |
| − | * From the '' | + | * From the ''Start Page'', click ''Manage Passwords''. |
* The context names of the app passwords created so far are listed. | * The context names of the app passwords created so far are listed. | ||
*: [[File:App_passwords_manage.png|center|400px]] | *: [[File:App_passwords_manage.png|center|400px]] | ||
* Click ''Add'' to add a new app password. | * Click ''Add'' to add a new app password. | ||
*: [[File:App_passwords_create.png|center|400px]] | *: [[File:App_passwords_create.png|center|400px]] | ||
| + | * App password context names must be unique and cannot contain the app password. | ||
* Highlight a name and click ''Delete'' to delete an app password. | * Highlight a name and click ''Delete'' to delete an app password. | ||
[[de:Multi-Faktor-Authentifizierung]] | [[de:Multi-Faktor-Authentifizierung]] | ||
| − | [[en:Multi- | + | [[en:Multi-factor_Authentication]] |
Latest revision as of 12:09, 28 March 2024
To increase security during the login process, multi-factor authentication (MFA) can be activated for MailStore users. MailStore supports Time-based One-time Password (TOTP) according to RFC 6238.
To do this, users need a TOTP-capable device, e.g. a smartphone with an installed authenticator app.
MailStore does not request the second factor, when the user is authenticated by Windows Authentication (Single Sign-On) or OpenID Connect (Microsoft 365, ADFS, Google Workspace).
When MFA is enabled, users who authenticate against a directory service cannot utilize non-MFA-capable clients such as Scheduled Tasks, IMAP clients, or the Management API. This restriction is in place for security reasons. Due to MailStore’s internal management of app passwords (which are necessary for non-MFA-capable clients), a user could still log in to MailStore even if they are blocked in the directory service.
Important notice: In order for valid one-time passwords (TOTP) to be generated, the system times of the MailStore Server and the end devices must be synchronized.
Configuration
Administrators are able to configure multi-factor authentication within user management.
Log in as a MailStore administrator via MailStore Client. Click Administrative Tools > Users and Archives and then click Users.
Activation
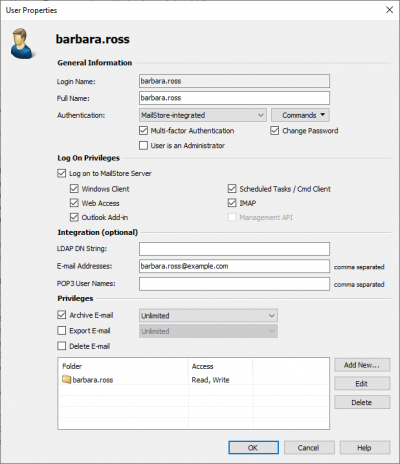
- Open the properties of the user you want to enable MFA for.
- Check the option Multi-factor Authentication in the General Information section.
- Confirm with OK.
- The next time the user logs in with an MFA-capable client (MailStore Client, MailStore Outlook Add-In, Web Access), the user will be prompted to scan a QR code with a TOTP-capable authenticator app (e.g. Google Authenticator), then enter an MFA code to complete the MFA configuration.
Deactivation
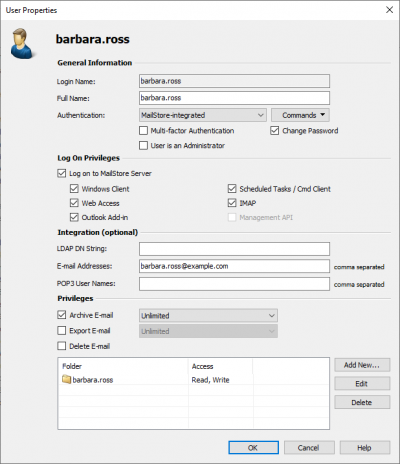
- Open the properties of the user you want to disable MFA for.
- Uncheck the option Multi-factor Authentication in the General Information section.
- Confirm with OK.
- App passwords that may have been created remain in place and remain valid.
Reinitialize MFA
If a user lost the device on which MFA was set up, wants to set up MFA on a different device, or needs to set up MFA again for some other reason, you can reinitialize MFA. This generates a new secret from which the one-time passwords are derived.
The next time the user logs in, they will be prompted again to complete the MFA configuration.
If the user has not yet completed the MFA configuration with their device, this function is not available.
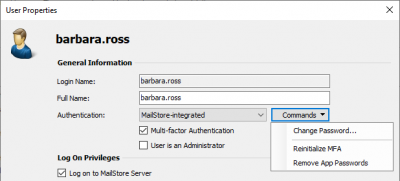
- Open the properties of the user you want to reinitialize MFA for.
- Click on the Commands button.
- Click on Reinitialize MFA.
- Confirm the operation.
Delete App passwords
If a user has created app passwords to continue using non MFA-capable clients (Scheduled Tasks, IMAP, Management API), you can delete them here.
If the user has not created any app passwords, this feature is not available.
App passwords can only be cleared in their entirety.
- Open the properties of the user whose app passwords you want to delete.
- Click the Commands button.
- Click on Remove App Passwords.
- Confirm the operation.
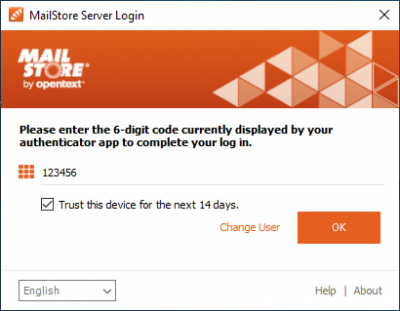
Login
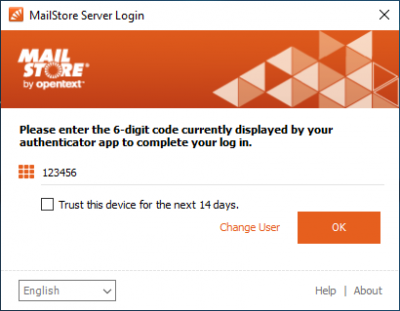
If multi-factor authentication has been activated for a user, the next time the user logs in with an MFA-capable client (MailStore Client, MailStore Outlook Add-In, Web Access), the user will be prompted to scan a QR code with a TOTP-capable authenticator app (e.g. Google Authenticator). This stores the previously generated secret into the app, and the app is able to generate valid one-time passwords.
The secret is displayed below the QR code and can be copied to the clipboard with a double-click to be stored in a password manager.
If the QR code has been scanned and a valid MFA code has been entered, subsequent login attempts will only be asked for the MFA code.
Trusted Devices
If the device from which the login is made is trusted, the option Trust this device for 14 days. can be set. When setting this option, an additional token is stored on the end device, which is sent with the login process.
MailStore Client, Outlook Add-In and Web Access each save their own token.
The token for MailStore Client and the Outlook Add-In is stored in the Windows credential manager. It does not move with roaming profiles.
The token for Web Access is stored in the browser's Local Storage. When Web Access is accessed in the browser's Incognito mode, the token is not persisted in between browser sessions.
Management of app passwords
Once multi-factor authentication has been enabled for a user, the normal password can no longer be used to log in with non MFA-capable clients.
Non MFA-capable clients include:
- Scheduled Tasks, that use the MailStore Client in command line mode
- IMAP clients
- Management-API clients, such as the Powershell API-Wrapper and the Python API-Wrapper
To ensure that these clients can still be used, users can create app passwords. These passwords are generated by MailStore and are characterized by increased complexity.
App passwords can only be managed via MailStore Client by users with MailStore-integrated authentication. In addition, the Change Password right is required.
App passwords work even with MFA disabled.
App passwords can never be used to login with MFA-capable clients.
- Log on to MailStore Client.
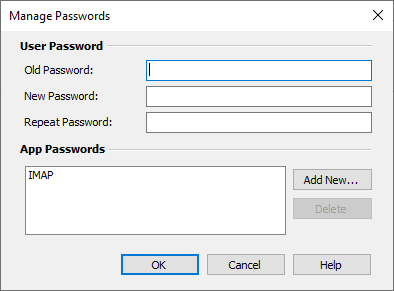
- From the Start Page, click Manage Passwords.
- The context names of the app passwords created so far are listed.
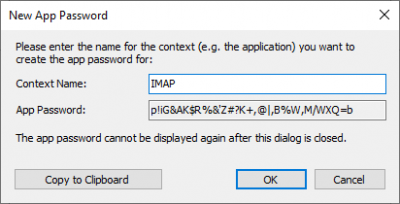
- Click Add to add a new app password.
- App password context names must be unique and cannot contain the app password.
- Highlight a name and click Delete to delete an app password.