Difference between revisions of "Using Lets Encrypt Certificates"
| [unchecked revision] | [checked revision] |
Ltalaschus (talk | contribs) |
|||
| (6 intermediate revisions by 2 users not shown) | |||
| Line 1: | Line 1: | ||
| + | {{DISPLAYTITLE:Using Let's Encrypt Certificates}} | ||
== Background == | == Background == | ||
| − | To ensure authenticity and security, MailStore Server uses TLS certificates in all provided services. During installation MailStore Server allows to either | + | To ensure authenticity and security, MailStore Server uses TLS certificates in all provided services. During installation, MailStore Server allows to either |
* create a self-signed certificate, | * create a self-signed certificate, | ||
| Line 6: | Line 7: | ||
* or obtain a certificate from Let's Encrypt. | * or obtain a certificate from Let's Encrypt. | ||
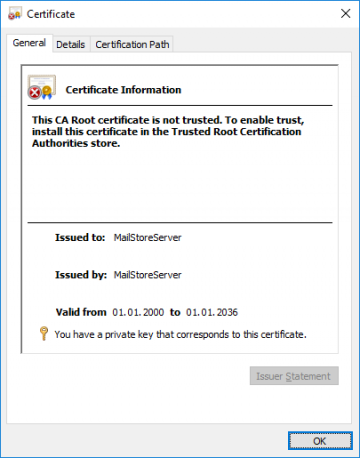
| − | The default choice of creating a self-signed certificate is often used when installing MailStore Server for the very first time, since | + | The default choice of creating a self-signed certificate is often used when installing MailStore Server for the very first time, since there are no external dependencies to be resolved. While this is perfectly fine in a non-production setup, it is not recommended for production use, because, without being signed by a trusted certificate authority, self-signed certificates are not trusted by other client computers. Furthermore, users might get used to ignoring certificate warnings, making them prone to man-in-the-middle attacks. |
| + | |||
| + | [[File:MScert.png|360px|center]] | ||
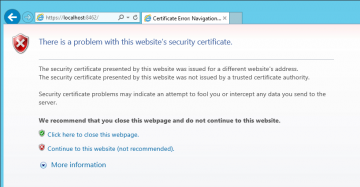
The following or a similar warning message is displayed when opening MailStore Web Access with a self-signed certificate in use. | The following or a similar warning message is displayed when opening MailStore Web Access with a self-signed certificate in use. | ||
| Line 12: | Line 15: | ||
[[File:MSnotrust.png|360px|center]] | [[File:MSnotrust.png|360px|center]] | ||
| − | To eliminate these warnings, increase security, | + | To eliminate these warnings, increase security, and enhance usability, MailStore Server needs to be configured to use a certificate that is signed by a trusted certificate authority. |
| − | The following describes how to obtain and use certificates from the free certificate authority Let's Encrypt. If you are already in possession of certificates ( | + | The following describes how to obtain and use certificates from the free certificate authority Let's Encrypt. If you are already in possession of trusted certificates (e.g. a wildcard certificate for your domain) or if you would like to manually request a certificate from your favorite CA, refer to [[Using Your Own SSL Certificate]] for detailed instructions. |
== About Let's Encrypt == | == About Let's Encrypt == | ||
| − | Let's Encrypt is a free, automated, and open certificate authority, trusted by all major web browsers and operating systems. Many large, well known sponsors from the IT industry support Let's Encrypt effort to help making the internet a safer place. | + | Let's Encrypt is a free, automated, and open certificate authority, trusted by all major web browsers and operating systems. Many large, well known sponsors from the IT industry support Let's Encrypt's effort to help making the internet a safer place. |
A fully automated certificate approval process eliminates email or phone verification of traditional certificate authorities that often take days. | A fully automated certificate approval process eliminates email or phone verification of traditional certificate authorities that often take days. | ||
| Line 24: | Line 27: | ||
== Prerequisites == | == Prerequisites == | ||
| − | * | + | * For the MailStore Server computer, a public DNS record (A or CNAME) must exist and point to a public IP address. |
| − | * The MailStore Server computer must be accessible from the Internet on TCP port 80 (HTTP) for Let's Encrypt's automatic domain approval process. A port forwarding on your firewall or gateway might be necessary. | + | * The MailStore Server computer must be accessible from the Internet on TCP port 80 (HTTP) for Let's Encrypt's automatic domain approval process. A port forwarding on your firewall or gateway might be necessary. Since Let's Encrypt validates from different IP addresses, such a firewall rule cannot be limited to certain source IP addresses. |
== Scenario 1: MailStore Server on Local Area Network (LAN) == | == Scenario 1: MailStore Server on Local Area Network (LAN) == | ||
| − | The most common scenario for a MailStore Server installation is on a local network inside the organization's premises. Typically the MailStore Server computer has a private IP address (e.g. 192.168.0.10) and the Internet connection is established through a router | + | The most common scenario for a MailStore Server installation is on a local network inside the organization's premises. Typically, the MailStore Server computer has a private IP address (e.g. 192.168.0.10) and the Internet connection is established through a router which masks all internal IP addresses with its own external IP address assigned by the ISP. This is known as Network Address Translation (NAT). |
For this scenario, we assume that MailStore Server is running on a new, dedicated computer. | For this scenario, we assume that MailStore Server is running on a new, dedicated computer. | ||
| Line 35: | Line 38: | ||
# Assign an available static IP Address from your local network to the MailStore Server computer. | # Assign an available static IP Address from your local network to the MailStore Server computer. | ||
# Create a port forwarding rule on the router, that forwards all connections to TCP port 80 on the public IP address, which was assigned in step 1, to the internal IP address of your MailStore Server computer assigned in step 2. | # Create a port forwarding rule on the router, that forwards all connections to TCP port 80 on the public IP address, which was assigned in step 1, to the internal IP address of your MailStore Server computer assigned in step 2. | ||
| − | # Add an A or CNAME record to the DNS zone of your public domain, e.g. mailstore.example.com pointing to the public IP address | + | #: '''Note:''' In the MailStore Server Service Configuration, you can change the ''Let's Encrypt HTTP-01 Challenge Port'' on which the MailStore Server service listens on the internal IP address assigned in step 2. However, on the public IP address assigned to the router in step 1, TCP port 80 must be used because Let's Encrypt's certificate approval process only supports this HTTP standard TCP port. If you change ''Let's Encrypt HTTP-01 Challenge Port'', you must update the port forwarding rule created in step 3 accordingly. |
| + | # Add an A or CNAME record to the DNS zone of your public domain, e.g. mailstore.example.com pointing to the public IP address that was assigned in step 1. | ||
# Depending on how DNS resolution is handled in your local network, you need to add a corresponding DNS record on your internal DNS server or router as well. This record should point to the internal IP address of the MailStore Server computer. | # Depending on how DNS resolution is handled in your local network, you need to add a corresponding DNS record on your internal DNS server or router as well. This record should point to the internal IP address of the MailStore Server computer. | ||
| Line 45: | Line 49: | ||
# Assign an available public IP Address from your public network to the MailStore Server computer. | # Assign an available public IP Address from your public network to the MailStore Server computer. | ||
# If there is a firewall in place, create a firewall rule, that allows all connections to TCP port 80 on the public IP address to pass through. | # If there is a firewall in place, create a firewall rule, that allows all connections to TCP port 80 on the public IP address to pass through. | ||
| − | # Add an A or CNAME record to the DNS zone of your public domain, e.g. mailstore.example.com pointing to the public IP address | + | #: '''Note:''' In the MailStore Server Service Configuration, you can change the ''Let's Encrypt HTTP-01 Challenge Port'' on which the MailStore Server service listens on the public IP address assigned in step 1. However, in the scenario described here, TCP port 80 must be used because Let's Encrypt's certificate approval process only supports this HTTP standard TCP port. |
| + | # Add an A or CNAME record to the DNS zone of your public domain, e.g. mailstore.example.com pointing to the public IP address that was assigned in step 1. | ||
== Obtaining the Certificate == | == Obtaining the Certificate == | ||
* Open the [[MailStore Server Service Configuration]]. | * Open the [[MailStore Server Service Configuration]]. | ||
| − | * Select ''Network Settings'' | + | * Select ''Network Settings''. |
| − | * In the certificate section, click on the ellipsis next to the certificate | + | * In the certificate section, click on the ellipsis next to the certificate. |
* Select ''Request from Let's Encrypt...'' | * Select ''Request from Let's Encrypt...'' | ||
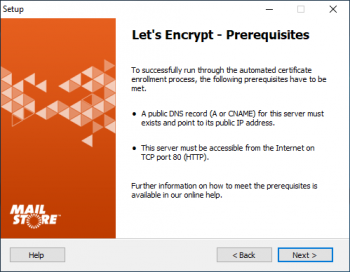
* The prerequisites are shown. | * The prerequisites are shown. | ||
| Line 56: | Line 61: | ||
* Click ''Next'' to proceed. | * Click ''Next'' to proceed. | ||
*: [[File:LetsEncryptRequest1.png|350px|center]] | *: [[File:LetsEncryptRequest1.png|350px|center]] | ||
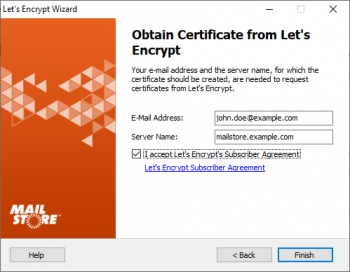
| − | * Enter your email address and the server name into the corresponding fields | + | * Enter your email address and the server name into the corresponding fields. |
* Click on the link to open the Let's Encrypt Subscriber Agreement. | * Click on the link to open the Let's Encrypt Subscriber Agreement. | ||
| − | * Once you have read and understood the Let's Encrypt Subscriber Agreement, tick the checkbox ''I accept Let's Encrypt's Subscriber Agreement'' | + | * Once you have read and understood the Let's Encrypt Subscriber Agreement, tick the checkbox ''I accept Let's Encrypt's Subscriber Agreement''. |
* Click ''Next'' to continue. | * Click ''Next'' to continue. | ||
* MailStore now tests the settings against Let's Encrypt's staging environment. If an issue occurs, MailStore will show a warning. Please review the log output, resolve the issue and try again. | * MailStore now tests the settings against Let's Encrypt's staging environment. If an issue occurs, MailStore will show a warning. Please review the log output, resolve the issue and try again. | ||
* If the test was successful, MailStore will automatically request a certificate from Let's Encrypt's production system and confirm that setup was successful. | * If the test was successful, MailStore will automatically request a certificate from Let's Encrypt's production system and confirm that setup was successful. | ||
* Click on ''Finish''. | * Click on ''Finish''. | ||
| + | * The automatic renewal of Let's Encrypt certificates every 60 days is active as long as no other certificate is selected manually. | ||
[[de:Verwendung_von_Lets_Encrypt_Zertifikaten]] | [[de:Verwendung_von_Lets_Encrypt_Zertifikaten]] | ||
[[en:Using Lets Encrypt Certificates]] | [[en:Using Lets Encrypt Certificates]] | ||
Latest revision as of 13:20, 12 November 2020
Background
To ensure authenticity and security, MailStore Server uses TLS certificates in all provided services. During installation, MailStore Server allows to either
- create a self-signed certificate,
- use an existing certificate,
- or obtain a certificate from Let's Encrypt.
The default choice of creating a self-signed certificate is often used when installing MailStore Server for the very first time, since there are no external dependencies to be resolved. While this is perfectly fine in a non-production setup, it is not recommended for production use, because, without being signed by a trusted certificate authority, self-signed certificates are not trusted by other client computers. Furthermore, users might get used to ignoring certificate warnings, making them prone to man-in-the-middle attacks.
The following or a similar warning message is displayed when opening MailStore Web Access with a self-signed certificate in use.
To eliminate these warnings, increase security, and enhance usability, MailStore Server needs to be configured to use a certificate that is signed by a trusted certificate authority.
The following describes how to obtain and use certificates from the free certificate authority Let's Encrypt. If you are already in possession of trusted certificates (e.g. a wildcard certificate for your domain) or if you would like to manually request a certificate from your favorite CA, refer to Using Your Own SSL Certificate for detailed instructions.
About Let's Encrypt
Let's Encrypt is a free, automated, and open certificate authority, trusted by all major web browsers and operating systems. Many large, well known sponsors from the IT industry support Let's Encrypt's effort to help making the internet a safer place.
A fully automated certificate approval process eliminates email or phone verification of traditional certificate authorities that often take days.
Let's Encrypt certificates are only valid for 90 days and thus need to be renewed regularly. The MailStore Server service handles the automatic renewals once the initial configuration is done.
Prerequisites
- For the MailStore Server computer, a public DNS record (A or CNAME) must exist and point to a public IP address.
- The MailStore Server computer must be accessible from the Internet on TCP port 80 (HTTP) for Let's Encrypt's automatic domain approval process. A port forwarding on your firewall or gateway might be necessary. Since Let's Encrypt validates from different IP addresses, such a firewall rule cannot be limited to certain source IP addresses.
Scenario 1: MailStore Server on Local Area Network (LAN)
The most common scenario for a MailStore Server installation is on a local network inside the organization's premises. Typically, the MailStore Server computer has a private IP address (e.g. 192.168.0.10) and the Internet connection is established through a router which masks all internal IP addresses with its own external IP address assigned by the ISP. This is known as Network Address Translation (NAT).
For this scenario, we assume that MailStore Server is running on a new, dedicated computer.
- Ask your Internet access provider to assign a static, public IP address to the router.
- Assign an available static IP Address from your local network to the MailStore Server computer.
- Create a port forwarding rule on the router, that forwards all connections to TCP port 80 on the public IP address, which was assigned in step 1, to the internal IP address of your MailStore Server computer assigned in step 2.
- Note: In the MailStore Server Service Configuration, you can change the Let's Encrypt HTTP-01 Challenge Port on which the MailStore Server service listens on the internal IP address assigned in step 2. However, on the public IP address assigned to the router in step 1, TCP port 80 must be used because Let's Encrypt's certificate approval process only supports this HTTP standard TCP port. If you change Let's Encrypt HTTP-01 Challenge Port, you must update the port forwarding rule created in step 3 accordingly.
- Add an A or CNAME record to the DNS zone of your public domain, e.g. mailstore.example.com pointing to the public IP address that was assigned in step 1.
- Depending on how DNS resolution is handled in your local network, you need to add a corresponding DNS record on your internal DNS server or router as well. This record should point to the internal IP address of the MailStore Server computer.
Scenario 2: MailStore Server on External Network
If the MailStore Server computer is already on a network that used public IP address, e.g. in a data center, or a DMZ it is much easier to fulfill the prerequisites.
For this scenario, we assume that MailStore Server is running on a new, dedicated computer.
- Assign an available public IP Address from your public network to the MailStore Server computer.
- If there is a firewall in place, create a firewall rule, that allows all connections to TCP port 80 on the public IP address to pass through.
- Note: In the MailStore Server Service Configuration, you can change the Let's Encrypt HTTP-01 Challenge Port on which the MailStore Server service listens on the public IP address assigned in step 1. However, in the scenario described here, TCP port 80 must be used because Let's Encrypt's certificate approval process only supports this HTTP standard TCP port.
- Add an A or CNAME record to the DNS zone of your public domain, e.g. mailstore.example.com pointing to the public IP address that was assigned in step 1.
Obtaining the Certificate
- Open the MailStore Server Service Configuration.
- Select Network Settings.
- In the certificate section, click on the ellipsis next to the certificate.
- Select Request from Let's Encrypt...
- The prerequisites are shown.
- Click Next to proceed.
- Enter your email address and the server name into the corresponding fields.
- Click on the link to open the Let's Encrypt Subscriber Agreement.
- Once you have read and understood the Let's Encrypt Subscriber Agreement, tick the checkbox I accept Let's Encrypt's Subscriber Agreement.
- Click Next to continue.
- MailStore now tests the settings against Let's Encrypt's staging environment. If an issue occurs, MailStore will show a warning. Please review the log output, resolve the issue and try again.
- If the test was successful, MailStore will automatically request a certificate from Let's Encrypt's production system and confirm that setup was successful.
- Click on Finish.
- The automatic renewal of Let's Encrypt certificates every 60 days is active as long as no other certificate is selected manually.