Difference between revisions of "Using Your Own SSL Certificate"
| [unchecked revision] | [unchecked revision] |
Ltalaschus (talk | contribs) |
|||
| Line 14: | Line 14: | ||
To configure MailStore Server for the use of your own certificate, please proceed as follows: | To configure MailStore Server for the use of your own certificate, please proceed as follows: | ||
| − | == Creating a Certificate Signing Request == | + | == Creating a Certificate Signing Request (CSR) == |
| − | Multiple tools are available to create a certificate signing request (CSR). | + | Multiple tools like OpenSSL, certreq and the MMC snap-in ''Certificates '' are available to create a certificate signing request (CSR). The following steps describe how to generate such a certificate signing request with ''certreq'' and how to import the resulting certificate into the windows certificate store. ''certreq'' is shipped with most windows versions. |
| − | + | * Log on to the MailStore Server computer. | |
| + | * Prepare a text file <tt>request.inf</tt> with the following content: | ||
| + | <pre> | ||
| + | ;----------------- request.inf ----------------- | ||
| + | [Version] | ||
| + | Signature="$Windows NT$" | ||
| − | * | + | [NewRequest] |
| − | * | + | ; replace Subject attributes in the line below with real values |
| − | * | + | Subject = "CN=mailarchive.example.com, OU=Department, O=Organisation, L=Locality, S=State, C=Country" |
| + | KeySpec = 1 | ||
| + | KeyLength = 2048 | ||
| + | Exportable = TRUE | ||
| + | FriendlyName = mailarchive.example.com | ||
| + | MachineKeySet = TRUE | ||
| + | SMIME = False | ||
| + | PrivateKeyArchive = FALSE | ||
| + | UserProtected = FALSE | ||
| + | UseExistingKeySet = FALSE | ||
| + | ProviderName = "Microsoft RSA SChannel Cryptographic Provider" | ||
| + | ProviderType = 12 | ||
| + | RequestType = PKCS10 | ||
| + | KeyUsage = 0xa0 | ||
| + | |||
| + | [EnhancedKeyUsageExtension] | ||
| + | OID = 1.3.6.1.5.5.7.3.1 ; this is for Server Authentication | ||
| + | </pre> | ||
| + | * Adjust the ''Subject'' and ''FriendlyName'' values according to your needs. | ||
| + | * Save the file. | ||
| + | * Open an elevated command prompt and navigate to the directory where the ''request.inf'' is stored. | ||
| + | * Create the CSR by executing the following command: | ||
| + | certreq -new request.inf request.csr | ||
| − | + | === ''Optional:'' Subject Alternative Names (SAN) === | |
| + | If the certificate should be valid for multiple host names, so called Subject Alternative Named (SAN) must be included in the CSR. Add the ''Extensions'' section as shown below to the the end of the <tt>request.inf</tt> file and adjust the host names to your needs or add additional ones by appending additional ''_continue_'' lines. Then save the file and create the request as explained previously. | ||
| − | + | <pre> | |
| + | [Extensions] | ||
| + | 2.5.29.17 = "{text}" | ||
| + | _continue_ = "DNS=mailarchive.example.com&" | ||
| + | _continue_ = "DNS=archive.example.com&" | ||
| + | </pre> | ||
| − | == | + | <p class="msnote">'''Important notice:''' When SANs are defined, the CN in the ''Subject'' field will be ignored by clients. Therefore all valid host names have to be added to the SAN extension.</p> |
| + | |||
| + | == Validating the Certificate Signing Request == | ||
| + | To verify that the CSR is correct, execute the following command to display it in a human readable format: | ||
| + | |||
| + | certutil -dump request.csr | ||
| + | |||
| + | == Submitting the Certificate Signing Request == | ||
| + | Submit the CSR to your preferred CA. Usually you upload the CSR file to a website of the CA. The CA might ask for the server platform during the submission process. Selecting ''IIS 7'' or ''None of the listed'' should be sufficient. After successful approval of the CSR, you will get the signed certificate in return. | ||
| + | |||
| + | <p class="msnote">'''Please note:''' Nowadays the certificate mostly is signed by intermediate CAs. It is required that the certificate of the intermediate CA is imported into the certificate store sign the require the installation of intermediate CA certificates. Detailed information about the installation process of intermediate CA certificates is typically included in the electronic delivery of your certificate.</p> | ||
| + | |||
| + | == ''Alternative 1:'' Importing the Certificate using certreq == | ||
| + | * Open an elevated command prompt and navigate to the directory where the certificate file is stored. | ||
| + | * Execute the following command to import the certificate into the computer's personal certificate store: | ||
| + | |||
| + | certreq -accept certificate.cer | ||
| + | |||
| + | * Use MMC's certificate snap-in or ''certlm.msc'' (Windows Server 2012 or newer only) to verify that the certificate has been imported properly in the computer's ''Personal'' certificate store and that a matching private key can be found. | ||
| + | |||
| + | [[File:Private_key.png|center]] | ||
| + | |||
| + | == ''Alternative 2:'' Importing the Certificate using MMC == | ||
* Log on to the server as administrator. | * Log on to the server as administrator. | ||
* Click on ''Start | Execute''. | * Click on ''Start | Execute''. | ||
| Line 50: | Line 105: | ||
* Confirm your entries and restart the MailStore Server service. | * Confirm your entries and restart the MailStore Server service. | ||
| + | == Appendix: Creating a PFX Container with OpenSSL == | ||
| + | When the CSR was created with OpenSSL, the private key is never stored in the Windows certificate store. To use certificates that have been created with OpenSSL in MailStore, it is therefore required to merge the private key, certificate and optionally the CA's certificate chain into a PFX container. This container can then be imported into Window's certificate store. | ||
| + | |||
| + | * Create the PFX container by executing the following command: | ||
| + | openssl pkcs12 -export -out certificate.pfx -inkey privateKey.key -in certificate.crt -certfile CACert.crt | ||
| + | * Open an elevated command prompt and navigate to the directory where the PFX file is stored. | ||
| + | * Import the content of the PFX container into the computer's personal certificate store by executing the following command: | ||
| + | certutil -importpfx certificate.pfx | ||
| + | |||
| + | == Weblinks == | ||
| + | * [https://technet.microsoft.com/en-us/library/dn296456.aspx Microsoft Technet: Certreq] | ||
| + | * [https://technet.microsoft.com/en-us/library/cc732443.aspx Microsoft Technet: Certutil] | ||
| + | * [https://technet.microsoft.com/de-de/library/ff625722.aspx Microsoft Technet: How to Request a Certificate With a Custom Subject Alternative Name] | ||
| + | * [https://www.openssl.org/docs/apps/openssl.html OpenSSL documentation] | ||
[[de:Verwendung_eigener_SSL_Zertifikate]] | [[de:Verwendung_eigener_SSL_Zertifikate]] | ||
[[en:Using Your Own SSL Certificate]] | [[en:Using Your Own SSL Certificate]] | ||
Revision as of 15:54, 29 January 2016
Background
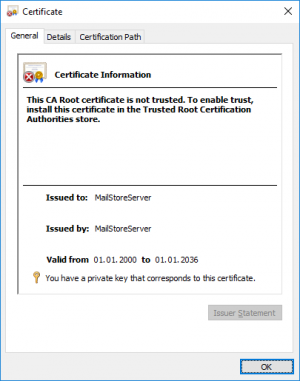
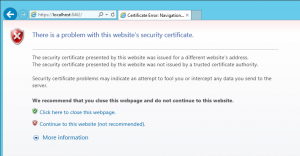
During the installation of MailStore Server, an SSL certificate is generated which all MailStore Server components use when an encrypted connection is to be established. Since the certificate is issued to the server name MailStoreServer and does not come from a reliable certification authority (CA), it is not trusted by the client side.
Because of this, the following warning message is displayed when calling up MailStore Web Access via HTTPS (SSL):
One option for resolving this issue is to make the server on which MailStore Server is installed available under the host name MailStoreServer (e.g. by adding an A- or CNAME record in the DNS) and installing the certificate in the container of trusted root certification authorities on the clients. Because these installations involve a relatively high administrative overhead, MailStore Server provides the option to use signed certificates of your own company CA or certificates of a public certification provider (e.g. VeriSign, eTrust etc.).
To configure MailStore Server for the use of your own certificate, please proceed as follows:
Creating a Certificate Signing Request (CSR)
Multiple tools like OpenSSL, certreq and the MMC snap-in Certificates are available to create a certificate signing request (CSR). The following steps describe how to generate such a certificate signing request with certreq and how to import the resulting certificate into the windows certificate store. certreq is shipped with most windows versions.
- Log on to the MailStore Server computer.
- Prepare a text file request.inf with the following content:
;----------------- request.inf ----------------- [Version] Signature="$Windows NT$" [NewRequest] ; replace Subject attributes in the line below with real values Subject = "CN=mailarchive.example.com, OU=Department, O=Organisation, L=Locality, S=State, C=Country" KeySpec = 1 KeyLength = 2048 Exportable = TRUE FriendlyName = mailarchive.example.com MachineKeySet = TRUE SMIME = False PrivateKeyArchive = FALSE UserProtected = FALSE UseExistingKeySet = FALSE ProviderName = "Microsoft RSA SChannel Cryptographic Provider" ProviderType = 12 RequestType = PKCS10 KeyUsage = 0xa0 [EnhancedKeyUsageExtension] OID = 1.3.6.1.5.5.7.3.1 ; this is for Server Authentication
- Adjust the Subject and FriendlyName values according to your needs.
- Save the file.
- Open an elevated command prompt and navigate to the directory where the request.inf is stored.
- Create the CSR by executing the following command:
certreq -new request.inf request.csr
Optional: Subject Alternative Names (SAN)
If the certificate should be valid for multiple host names, so called Subject Alternative Named (SAN) must be included in the CSR. Add the Extensions section as shown below to the the end of the request.inf file and adjust the host names to your needs or add additional ones by appending additional _continue_ lines. Then save the file and create the request as explained previously.
[Extensions]
2.5.29.17 = "{text}"
_continue_ = "DNS=mailarchive.example.com&"
_continue_ = "DNS=archive.example.com&"
Important notice: When SANs are defined, the CN in the Subject field will be ignored by clients. Therefore all valid host names have to be added to the SAN extension.
Validating the Certificate Signing Request
To verify that the CSR is correct, execute the following command to display it in a human readable format:
certutil -dump request.csr
Submitting the Certificate Signing Request
Submit the CSR to your preferred CA. Usually you upload the CSR file to a website of the CA. The CA might ask for the server platform during the submission process. Selecting IIS 7 or None of the listed should be sufficient. After successful approval of the CSR, you will get the signed certificate in return.
Please note: Nowadays the certificate mostly is signed by intermediate CAs. It is required that the certificate of the intermediate CA is imported into the certificate store sign the require the installation of intermediate CA certificates. Detailed information about the installation process of intermediate CA certificates is typically included in the electronic delivery of your certificate.
Alternative 1: Importing the Certificate using certreq
- Open an elevated command prompt and navigate to the directory where the certificate file is stored.
- Execute the following command to import the certificate into the computer's personal certificate store:
certreq -accept certificate.cer
- Use MMC's certificate snap-in or certlm.msc (Windows Server 2012 or newer only) to verify that the certificate has been imported properly in the computer's Personal certificate store and that a matching private key can be found.
Alternative 2: Importing the Certificate using MMC
- Log on to the server as administrator.
- Click on Start | Execute.
- Execute the command mmc.
- Select File | Add/Remove Snap-In | Add | Certificate.
- Select Local Computer Account and then Local Computer.
- Click on Finish and close any open dialog windows.
- In the management console, select My Certificates | Certificates.
- Right-click on the folder Certificates and select All Tasks | Import.
- Follow the instructions in the wizard and select the file containing the certificate and the private key, if applicable.
- On the page Certificate Store select the container My Certificates and finish the wizard.
- The certificate is now shown in the container My Certificates.
- To verify this and to make sure that the private key for the certificate is available, open the certificate with a double-click.
Using the Certificate with MailStore Server
- Open the MailStore Server Service Configuration.
- Select IP Addresses and Ports.
- In the section you want to change to certificate for, click on the button next to the Server Certificate field and select Select from Certificate Store...
- Choose the new certificate from the certificate store.
- Confirm your entries and restart the MailStore Server service.
Appendix: Creating a PFX Container with OpenSSL
When the CSR was created with OpenSSL, the private key is never stored in the Windows certificate store. To use certificates that have been created with OpenSSL in MailStore, it is therefore required to merge the private key, certificate and optionally the CA's certificate chain into a PFX container. This container can then be imported into Window's certificate store.
- Create the PFX container by executing the following command:
openssl pkcs12 -export -out certificate.pfx -inkey privateKey.key -in certificate.crt -certfile CACert.crt
- Open an elevated command prompt and navigate to the directory where the PFX file is stored.
- Import the content of the PFX container into the computer's personal certificate store by executing the following command:
certutil -importpfx certificate.pfx