Difference between revisions of "Multi Server Mode Setup"
| [checked revision] | [checked revision] |
Ltalaschus (talk | contribs) |
Ltalaschus (talk | contribs) (MFA hint added) |
||
| Line 99: | Line 99: | ||
* Click ''Pair with this server''. | * Click ''Pair with this server''. | ||
* Enter the user name and password of a MailStore Service Provider Edition administrator. | * Enter the user name and password of a MailStore Service Provider Edition administrator. | ||
| + | : '''Note:''' When MFA is enabled for this administrator, an API password must be created and entered here to successfully pair the role with the ''Management Server''. More about MFA can be found on the [[Management_Console_-_Your_MFA_Settings|Your MFA Settings]] documentation page. | ||
* Click ''OK'' to pair this role with the Management Server. | * Click ''OK'' to pair this role with the Management Server. | ||
* The fingerprint of the Management Server's TLS certificate is copied in the ''Management Server Cert'' field of the role to be installed. | * The fingerprint of the Management Server's TLS certificate is copied in the ''Management Server Cert'' field of the role to be installed. | ||
Latest revision as of 13:52, 14 November 2022
Multi Server Mode Setup
When setting up MailStore Service Provider Edition in multi server mode, the first role to set up must always be the Management Server role. Afterwards one or multiple Instance Hosts and Client Access Servers can be set up. Each server in a multi server mode setup can host one or multiple roles.
Set Up Management Server
- If not executed automatically by the installation program, start the MailStore Service Provider Edition Configuration tool by double-clicking its desktop icon. On a Windows Server Core use the command line prompt to start the executable (default: %PROGRAMFILES%\MailStore Infrastructure\MailStoreInfrastructureConfig.exe.
- If no configuration files and services are found, the MailStore Service Provider Edition Configuration will ask for the desired mode. Select Multi Server Mode and click OK.
- Click Add Server Role
- Select Management Server
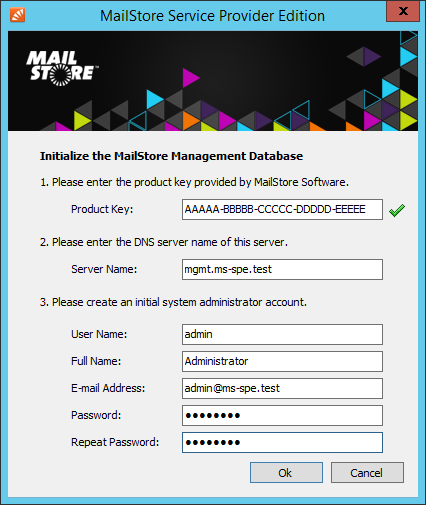
- Enter your product key into the Product Key field and change Server Name to the fully qualified host name of the server (e.g. mgmt.ms-spe.test). Enter the user name , the full name (optional), the email address and the password of the initial administrator account that will be used to log on to the Management Console.
Important notice: Changing the host name after the Management Server has been configured requires additional, mostly manual actions such as transferring the license, re-pairing Instance Hosts and Client Access Servers and making changes to the configuration database. Therefore it is recommend to not change the host name afterwards.
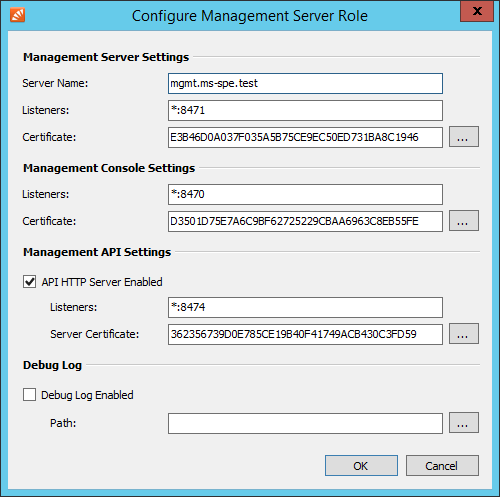
- Fill out the Configure Management Server Role form.
- Management Server Settings
- Server Name: Fully qualified host name (FQHN) of the server
- Listeners: If the server is multihomed you can specify on which IP address and TCP port to listen for incoming connections from Instance Hosts and Client Access Servers (Default: *:8471)
- Certificate: Fingerprint of the TLS certificate used by the Management Server to authenticate against Instance Hosts and Client Access Serves. Use the button next to the fingerprint to select a different certificate from the computer's certificate store.
- Management Console Settings
- Listeners: If the server is multihomed you can specify on which IP address and TCP port to listen for incoming connections to the Management Console (Default: *:8470)
- Certificate: Fingerprint of the TLS certificate used by the Management Server's HTTP server. Use the button next to the fingerprint to select a different certificate from the computer's certificate store.
- Management API Settings
- The Management API needs to be active when Instance Hosts or Client Access Servers will be paired with this Management Server.
- Listeners: If the server is multihomed you can specify on which IP address and TCP port to listen for incoming connections to the Management Console and Management API (Default: *:8470)
- Certificate: Fingerprint of the TLS certificate used by the Management Server's API server. Use the button next to the fingerprint to select a different certificate from the computer's certificate store.
- Debug Log
- In case of errors the debug log of the Management Server can be enabled here.
- Path: Directory on the file system where the debug log files are written into.
- Click OK to add the Management Server role.
- Click Start to start the Management Server service.
- Please note: As the startup process of the services is asynchronous, please wait up to 30 seconds. A service shown as running may still switch back to stopped during that period if an error occurred.
- It is now safe to close the MailStore Service Provider Edition Configuration tool
Set Up Instance Host
- If not executed automatically by the installation program, start the MailStore Service Provider Edition Configuration tool by double-clicking its desktop icon. On a Windows Server Core use the command line prompt to start the executable (default: %PROGRAMFILES%\MailStore Infrastructure\MailStoreInfrastructureConfig.exe.
- If no configuration files and services are found, the MailStore Service Provider Edition Configuration will ask for the desired mode. Select Multi Server Mode and click OK.
- Click Add Server Role
- Select Instance Host
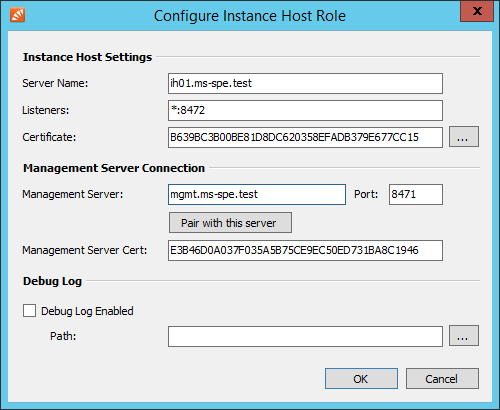
- Fill out the Configure Instance Host Role form.
- Instance Host Settings
- Server Name: Fully qualified host name (FQHN) of the server
- Listeners: If the server is multihomed you can specify on which IP address and TCP port to listen for incoming connections from the Management Server (Default: *:8472)
- Certificate: Fingerprint of the TLS certificate used by the Instance Host to authenticate against Management Server. Use the button next to the fingerprint to select a different certificate from the computer's certificate store.
- Management Server Connection
- Management Server: Fully qualified host name (FQHN) of the Management Server to connect to.
- Port: TCP port where the above Management Server accepts incoming connections.
- Management Server Cert: Fingerprint of the TSL certificate used by the Management Server to authenticate against Instance Host. This value is set automatically when Pairing with Management Server
- Debug Log
- In case of errors the debug log of the Instance Host can be enabled here.
- Path: Directory on the file system where the debug log files are written into.
- Click OK to add the Instance Host role.
- Click Start to start the Instance Host service.
- Please note: As the startup process of the services is asynchronous, please wait up to 30 seconds. A service shown as running may still switch back to stopped during that period if an error occurred.
- It is now safe to close the MailStore Service Provider Edition Configuration tool
Set Up Client Access Server
- If not executed automatically by the installation program, start the MailStore Service Provider Edition Configuration tool by double-clicking its desktop icon. On a Windows Server Core use the command line prompt to start the executable (default: %PROGRAMFILES%\MailStore Infrastructure\MailStoreInfrastructureConfig.exe.
- If no configuration files and services are found, the MailStore Service Provider Edition Configuration will ask for the desired mode. Select Multi Server Mode and click OK.
- Click Add Server Role .
- Select Client Access Server.
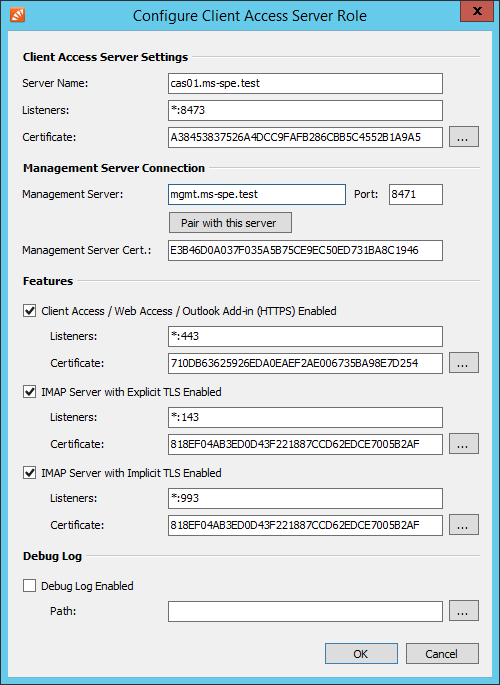
- Fill out the Configure Client Access Server Role form.
- Client Access Server Settings
- Server Name: Fully qualified host name (FQHN) of the server
- Listeners: If the server is multihomed you can specify on which IP address and TCP port to listen for incoming connections from the Management Server (Default: *:8473)
- Certificate: Fingerprint of the TLS certificate used by the Client Access Server to authenticate against Management Server. Use the button next to the fingerprint to select a different certificate from the computer's certificate store.
- Management Server Connection
- Management Server: Fully qualified host name (FQHN) of the Management Server to connect to.
- Port: TCP port where the above Management Server accepts incoming connections.
- Management Server Cert: Fingerprint of the TLS certificate used by the Management Server to authenticate against Client Access Server. This value is set automatically when Pairing with Management Server
- Features
- Client Access / Web Access / Outlook Add-in (HTTPS) Enabled: If enabled the Client Access Server provides access to archives via MailStore Client, MailStore Outlook Add-in and MailStore Web Access.
- Listeners: If the server is multihomed you can specify on which IP address and TCP port to listen for incoming connections (Default: *:443)
- Certificate: Fingerprint of the TLS certificate used by the HTTP Server. Use the button next to the fingerprint to select a different certificate from the computer's certificate store.
- IMAP Server with explicit TLS Enabled: If enabled the Client Access Server provides access to archives via IMAP protocol. Connections must be secured via STARTTLS.
- Listeners: If the server is multihomed you can specify on which IP address and TCP port to listen for incoming connections (Default: *:143)
- Certificate: Fingerprint of the TLS certificate used by the IMAP Server. Use the button next to the fingerprint to select a different certificate from the computer's certificate store.
- IMAP Server with implicit TLS Enabled: If enabled the Client Access Server provides access to archives via IMAP protocol. Connection is encrypted via SSL/TLS.
- Listeners: If the server is multihomed you can specify on which IP address and TCP port to listen for incoming connections (Default: *:993)
- Certificate: Fingerprint of the TLS certificate used by the IMAP Server. Use the button next to the fingerprint to select a different certificate from the computer's certificate store.
- Debug Log
- In case of errors the debug log of the Client Access Server can be enabled here.
- Path: Directory on the file system where the debug log files are written into.
- Click OK to add the Client Access Server role.
- Click Start to start the Client Access Server service.
- Please note: As the startup process of the services is asynchronous, please wait up to 30 seconds. A service shown as running may still switch back to stopped during that period if an error occurred.
- It is now safe to close the MailStore Service Provider Edition Configuration tool
Pairing with Management Server
Before Client Access Servers and Instance Hosts are able to communicate with the Management Server, TLS certificate fingerprints must be exchanged to establish a trust relationship. Additionally the Instance Hosts and Client Access Servers must be registered in the Management Server with its server name and TCP port.
This process can simply be performed by using the pairing function as described in the following:
- Enter the fully qualified host name of the server where the role is added in the Server Name field.
- Enter the fully qualified host name of the Management Server in the corresponding Management Server field while configuring an Instance Host or Client Access Server.
- Click Pair with this server.
- Enter the user name and password of a MailStore Service Provider Edition administrator.
- Note: When MFA is enabled for this administrator, an API password must be created and entered here to successfully pair the role with the Management Server. More about MFA can be found on the Your MFA Settings documentation page.
- Click OK to pair this role with the Management Server.
- The fingerprint of the Management Server's TLS certificate is copied in the Management Server Cert field of the role to be installed.
- The fingerprint of the role's TCP server's TLS certificate is transferred to the Management Database of the Management Server. This can be reviewed here.
Please note: Pairing is carried out through the Management API. Therefore the Management API must be enabled on the Management Server and the Instance Hosts and Client Access Servers must be able to establish a connection to the API on the Management Server (Default TCP port: 8474).
If your security policy does not permit establishing such a connection, pairing must be performed manually. Please refer to Add New Instance Host or Add New Client Access Server for further details.