Difference between revisions of "Replace Self-signed SSL Certificates"
| [checked revision] | [checked revision] |
Ltalaschus (talk | contribs) |
Ltalaschus (talk | contribs) |
||
| (5 intermediate revisions by 3 users not shown) | |||
| Line 1: | Line 1: | ||
MailStore Service Provider Edition automatically creates self-signed certificates when adding a new role to a server. While these certificates are suitable for authenticating MailStore Service Provider Edition's own services against each other by storing and verifying the unique fingerprints of the used certificates, self-signed certificates are not suitable for public internet services like email or web servers. | MailStore Service Provider Edition automatically creates self-signed certificates when adding a new role to a server. While these certificates are suitable for authenticating MailStore Service Provider Edition's own services against each other by storing and verifying the unique fingerprints of the used certificates, self-signed certificates are not suitable for public internet services like email or web servers. | ||
| − | Therefore it is recommended to replace the SSL certificates used by the Client Access Servers for offering IMAP and web based access to the archives with certificates signed by an official certificate authority. | + | Therefore it is recommended to replace the SSL certificates used by the Client Access Servers for offering IMAP and web based access to the archives with certificates signed by an official certificate authority. Information on requesting, renewing and working with such certificates can be found in this [[Working_with_SSL_Certificates|article]]. |
| + | |||
| + | It usually is not necessary to replace the certificates that are used by MailStore Service Provider Edition for the internal communication. These certificates are configured in the ''Client Access Server Settings'' and ''Instance Host Settings'' sections of the role configuration dialog. If you would change these certificates, you also have to [[Multi_Server_Mode_Setup#Pairing_with_Management_Server|pair]] your ''Client Access Server'' or ''Instance Host'' with the ''Management Server'' to gain trust again. | ||
== Prerequisites == | == Prerequisites == | ||
| Line 11: | Line 13: | ||
* Click ''Configure..''. | * Click ''Configure..''. | ||
* For each endpoint in the ''Features'' section (HTTP, IMAP, IMAPS) click on the button behind the '''Certificate'' field to select the new certificate from the Windows certificate store. | * For each endpoint in the ''Features'' section (HTTP, IMAP, IMAPS) click on the button behind the '''Certificate'' field to select the new certificate from the Windows certificate store. | ||
| − | *; '''Please note:''' | + | *; [[File:Ms_spe_replace_self_signed_cert_01.png]] |
| + | *; '''Please note:''' It is not required to replace the ''Certificate'' under the ''Client Access Server Settings''. If you would change this certificate, you also have to [[Multi_Server_Mode_Setup#Pairing_with_Management_Server|pair]] your ''CAS'' with the ''Management Server'' to gain trust again. | ||
* Click ''OK'' to save changes or ''Cancel'' to discard. | * Click ''OK'' to save changes or ''Cancel'' to discard. | ||
* Start the Client Access Server. | * Start the Client Access Server. | ||
Repeat the above on each Client Access Server in your MailStore Service Provider Edition infrastructure. | Repeat the above on each Client Access Server in your MailStore Service Provider Edition infrastructure. | ||
Latest revision as of 15:35, 30 January 2024
MailStore Service Provider Edition automatically creates self-signed certificates when adding a new role to a server. While these certificates are suitable for authenticating MailStore Service Provider Edition's own services against each other by storing and verifying the unique fingerprints of the used certificates, self-signed certificates are not suitable for public internet services like email or web servers.
Therefore it is recommended to replace the SSL certificates used by the Client Access Servers for offering IMAP and web based access to the archives with certificates signed by an official certificate authority. Information on requesting, renewing and working with such certificates can be found in this article.
It usually is not necessary to replace the certificates that are used by MailStore Service Provider Edition for the internal communication. These certificates are configured in the Client Access Server Settings and Instance Host Settings sections of the role configuration dialog. If you would change these certificates, you also have to pair your Client Access Server or Instance Host with the Management Server to gain trust again.
Prerequisites
Before a certificate can be used by the Client Access Server service, the certificate and its private key must be stored in the computer's personal/MY certificate store (not Administrator's or any other user's).
Installing New Certificates
- Start the MailStore Service Provider Edition Configuration tool on a server that is a Client Access Server by double-clicking it's desktop icon. On Windows Server Core use the command line prompt to start the executable (default: %PROGRAMFILES%\MailStore Infrastructure\MailStoreInfrastructureConfig.exe.
- Stop the Client Access Server.
- Click Configure...
- For each endpoint in the Features section (HTTP, IMAP, IMAPS) click on the button behind the 'Certificate field to select the new certificate from the Windows certificate store.
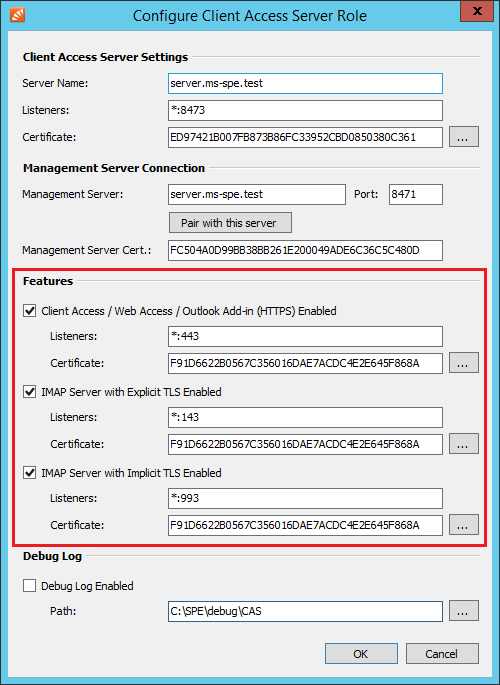
- Please note: It is not required to replace the Certificate under the Client Access Server Settings. If you would change this certificate, you also have to pair your CAS with the Management Server to gain trust again.
- Click OK to save changes or Cancel to discard.
- Start the Client Access Server.
Repeat the above on each Client Access Server in your MailStore Service Provider Edition infrastructure.
